How Secure is Wasabi?
How Secure is Wasabi?
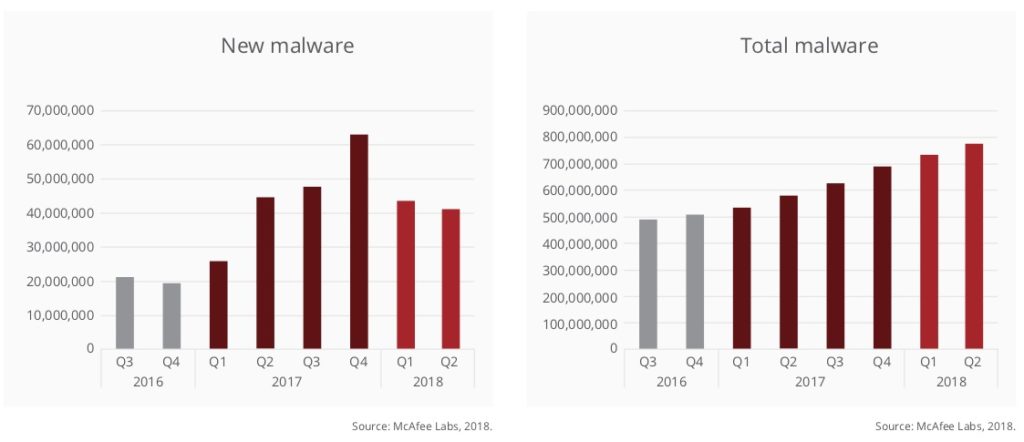
Cybersecurity is top of mind for just about every CIO I meet. All over the world, cyber threats continue to grow in frequency, complexity and severity. Just take a look at these global malware charts from last month’s McAfee Labs Threats Report.
Security breaches can tarnish your brand and harm your business. According to Cisco’s 2018 Annual Cybersecurity Report, over half of cyberattacks result in damages of $500,000 or more when you factor in lost revenue and other opportunity costs.
Wasabi hot cloud storage is designed from the ground up to protect your data and keep your business up and running. The service is engineered to provide high availability, protect data privacy, and defend against ransomware and other forms of malware that can paralyze operations and impact your bottom line. In this blog, I’ll review the strong security systems and practices Wasabi uses to safeguard your data and protect your business.
Wasabi’s Defense-in-Depth Security Protects Against a Wide Range of Threats
Cybersecurity experts like the National Security Agency recommend a layered “defense-in-depth” approach to security to contain attacks and defend against the widest range of cyber threats. To that end, the entire Wasabi operating environment is built and managed with security best practices and standards in mind. We ensure the physical security of our data centers; employ strong authentication, authorization and accounting controls for all of our cloud compute, storage and networking infrastructure; encrypt data at rest and data in transit to prevent unauthorized disclosure; and support an optional data immutability capability to protect data against ransomware and other forms of malware.
- Physical Security – Wasabi is hosted in SOC 2 and ISO 27001 data centers that are highly secure and fully redundant. Each facility is guarded round-the-clock by on-site security staff.
- Network Security – We use a variety of network security elements to monitor and control communications at internal and external network borders. These edge security devices segregate customers and restrict the flow of communications between networks to prevent unauthorized access to Wasabi infrastructure and services.
- Data Privacy – Wasabi encrypts data at rest using methods described in this article. In addition, we encrypt data in transit using HTTPS. Our customers are also welcome to encrypt their own data prior to sending it to Wasabi.
- User Authentication and Authorization Controls – We support strong user passwords to control access to stored data. We also support access control lists and role-based policies that let you selectively grant permissions (e.g. read-only, write-only, read/write, admin) to individual users, groups of users or classes of users.
- Data Immutability – Wasabi supports an optional data immutability feature to mitigate ransomware and other types of malware. Data written to an immutable Wasabi storage bucket cannot be deleted or altered by anyone (including Wasabi) throughout its storage lifetime.
- Security Audit Trails – We provide detailed access logs for security audits and threat remediation. Log records contain information about each access request such as the request type, accessed resources, date and time.
Wasabi’s strong security systems and practices can help you protect the integrity of your data, and avoid downtime and data loss. The service is designed to comply with government data privacy and retention regulations including various CJIS, FERPA, FINRA, GDPR, HIPAA and SEC rules.
To learn more about our security features and capabilities please download our Wasabi’s Strong Security Systems and Practices tech brief.
the bucket
Cybersecurity is top of mind for just about every CIO I meet. All over the world, cyber threats continue to grow in frequency, complexity and severity. Just take a look at these global malware charts from last month’s McAfee Labs Threats Report.
Security breaches can tarnish your brand and harm your business. According to Cisco’s 2018 Annual Cybersecurity Report, over half of cyberattacks result in damages of $500,000 or more when you factor in lost revenue and other opportunity costs.
Wasabi hot cloud storage is designed from the ground up to protect your data and keep your business up and running. The service is engineered to provide high availability, protect data privacy, and defend against ransomware and other forms of malware that can paralyze operations and impact your bottom line. In this blog, I’ll review the strong security systems and practices Wasabi uses to safeguard your data and protect your business.
Wasabi’s Defense-in-Depth Security Protects Against a Wide Range of Threats
Cybersecurity experts like the National Security Agency recommend a layered “defense-in-depth” approach to security to contain attacks and defend against the widest range of cyber threats. To that end, the entire Wasabi operating environment is built and managed with security best practices and standards in mind. We ensure the physical security of our data centers; employ strong authentication, authorization and accounting controls for all of our cloud compute, storage and networking infrastructure; encrypt data at rest and data in transit to prevent unauthorized disclosure; and support an optional data immutability capability to protect data against ransomware and other forms of malware.
- Physical Security – Wasabi is hosted in SOC 2 and ISO 27001 data centers that are highly secure and fully redundant. Each facility is guarded round-the-clock by on-site security staff.
- Network Security – We use a variety of network security elements to monitor and control communications at internal and external network borders. These edge security devices segregate customers and restrict the flow of communications between networks to prevent unauthorized access to Wasabi infrastructure and services.
- Data Privacy – Wasabi encrypts data at rest using methods described in this article. In addition, we encrypt data in transit using HTTPS. Our customers are also welcome to encrypt their own data prior to sending it to Wasabi.
- User Authentication and Authorization Controls – We support strong user passwords to control access to stored data. We also support access control lists and role-based policies that let you selectively grant permissions (e.g. read-only, write-only, read/write, admin) to individual users, groups of users or classes of users.
- Data Immutability – Wasabi supports an optional data immutability feature to mitigate ransomware and other types of malware. Data written to an immutable Wasabi storage bucket cannot be deleted or altered by anyone (including Wasabi) throughout its storage lifetime.
- Security Audit Trails – We provide detailed access logs for security audits and threat remediation. Log records contain information about each access request such as the request type, accessed resources, date and time.
Wasabi’s strong security systems and practices can help you protect the integrity of your data, and avoid downtime and data loss. The service is designed to comply with government data privacy and retention regulations including various CJIS, FERPA, FINRA, GDPR, HIPAA and SEC rules.
To learn more about our security features and capabilities please download our Wasabi’s Strong Security Systems and Practices tech brief.
featured articles
THE CHANNEL TECH PARTNERS
January 24, 2024
Announcing the Winners of our 2023 Partner Awards
Announcing the Winners of our 2023 Partner Awards
WASABI TECHNOLOGY
January 23, 2024
A Letter from the CEO: On Wasabi’s Acquisition of C...
A Letter from the CEO: On Wasabi’s Acquisition of ...
VIDEO SURVEILLANCE
January 25, 2024
Navigating the Future: The Evolution of Security In...
Navigating the Future: The Evolution of Security I...
DATA MANAGEMENT CASE STUDY
January 22, 2024
Australian MSP Office Solutions IT Migrates Service...
Australian MSP Office Solutions IT Migrates Servic...
COMPLIANCE CASE STUDY
January 17, 2024